Bluetooth Low Energy Devices Security Testing Framework

You can also view the signal strength rssi in real time to get an idea of how close you.
Bluetooth low energy devices security testing framework. Security mode 1 devices never initiate security and therefore should never be used. Ble remains in sleep mode when not connected. This technology also known as the abbreviation ble is establishing itself for connected devices as it is ideal to send small amounts of data between devices and to preserve the battery. Zigbee is an ieee 802 15 4 based specification for a suite of high level communication protocols used to create personal area networks with small low power digital radios such as for home automation medical device data collection and other low power low bandwidth needs designed for small scale projects which need wireless connection hence zigbee is a low power low data rate and close.
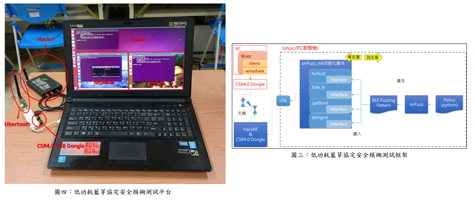
Alternative to classic bluetooth bluetooth low energy is chosen increasingly for the iot. Lightblue can connect you to all of your devices that use bluetooth low energy also known as bluetooth smart or bluetooth light. All tested devices are vulnerable and this confirms that there is a need for better security testing tools as well as for additional. Key method it also presents a framework for defining and executing ble security attacks and evaluates it on three ble devices.
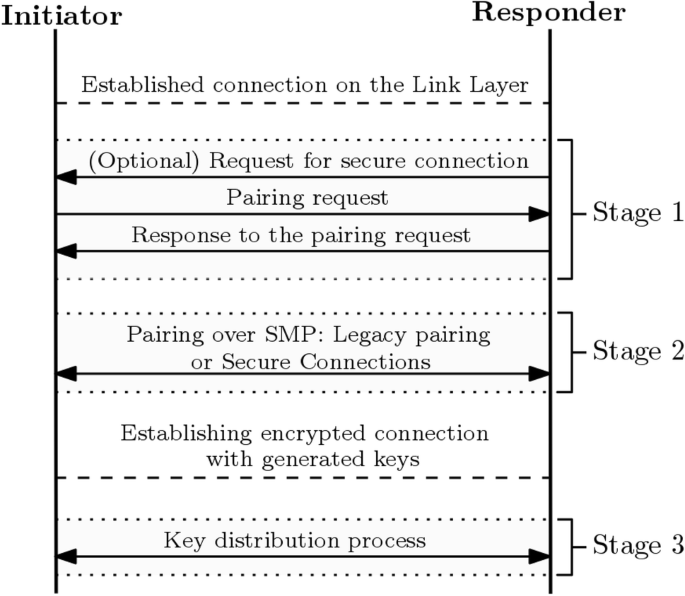
By september they had found their first bug in certain implementations of bluetooth low energy the version of the protocol designed for devices with limited resources and power. Discusses security considerations for devices that might implement bluetooth or bluetooth low energy communication protocols. Bluetooth low energy ble available in android 4 3 and later creates short connections between devices to transfer bursts of data. For the low energy feature of bluetooth introduced in version 4 0 and updated in 4 1 and 4 2 security mode 1 level 4 is the strongest mode because it requires authenticated low energy secure.
Full support of read write and notify is included to ease ble firmware development efforts. Don t subclass any of the classes of the core bluetooth framework. Bluetooth low energy ble a low power wireless protocol is widely used in industrial automation for monitoring field devices. With lightblue you can scan connect to and browse any nearby ble device.
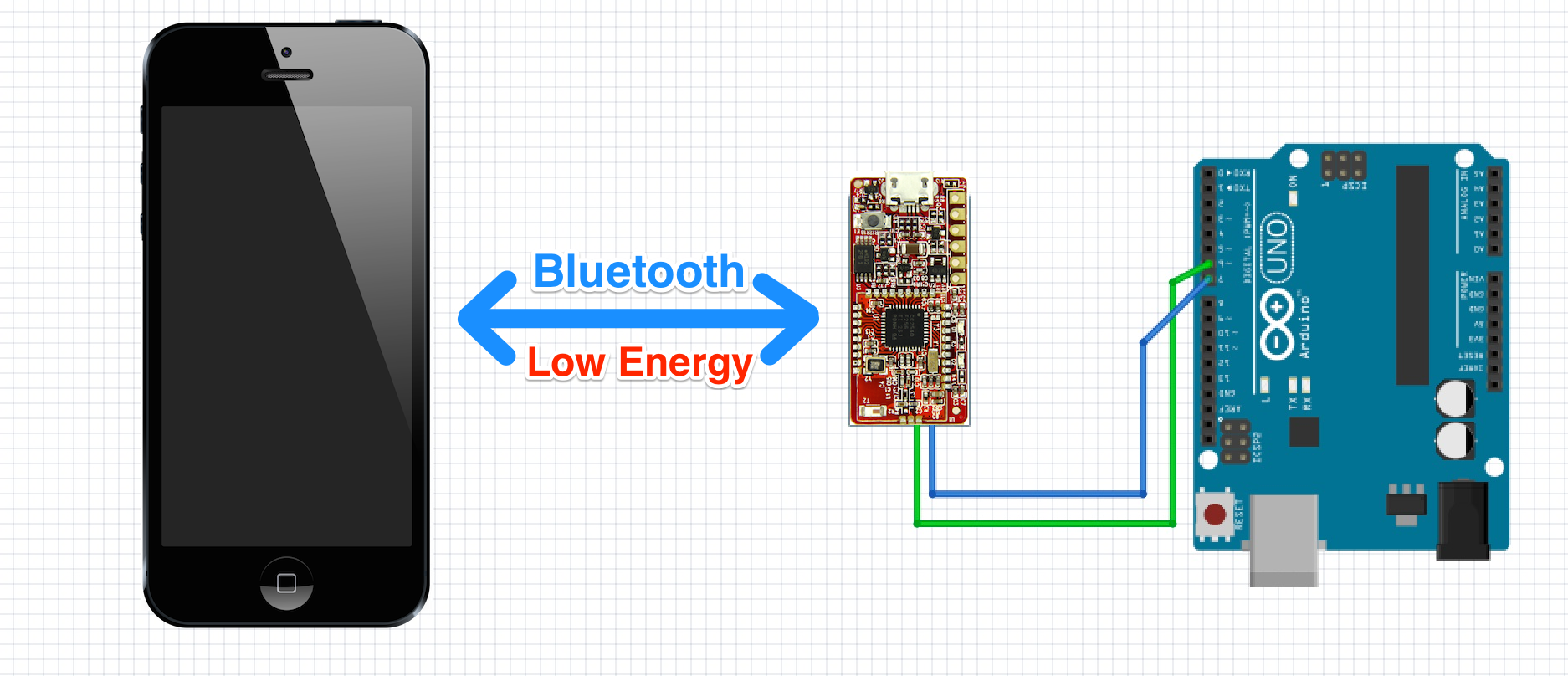
Bluetooth low energy is distinct from the previous often called classic bluetooth basic rate enhanced data rate br edr protocol but the two protocols can both be supported by one device. Foundational activities and core device cybersecurity capability baseline ble bluetooth special publication 800 121 revision 2. The bluetooth 4 0 specification permits devices to implement either or both of the le and br edr systems. This lets ble provide lower bandwidth and reduced power consumption compared to classic bluetooth.
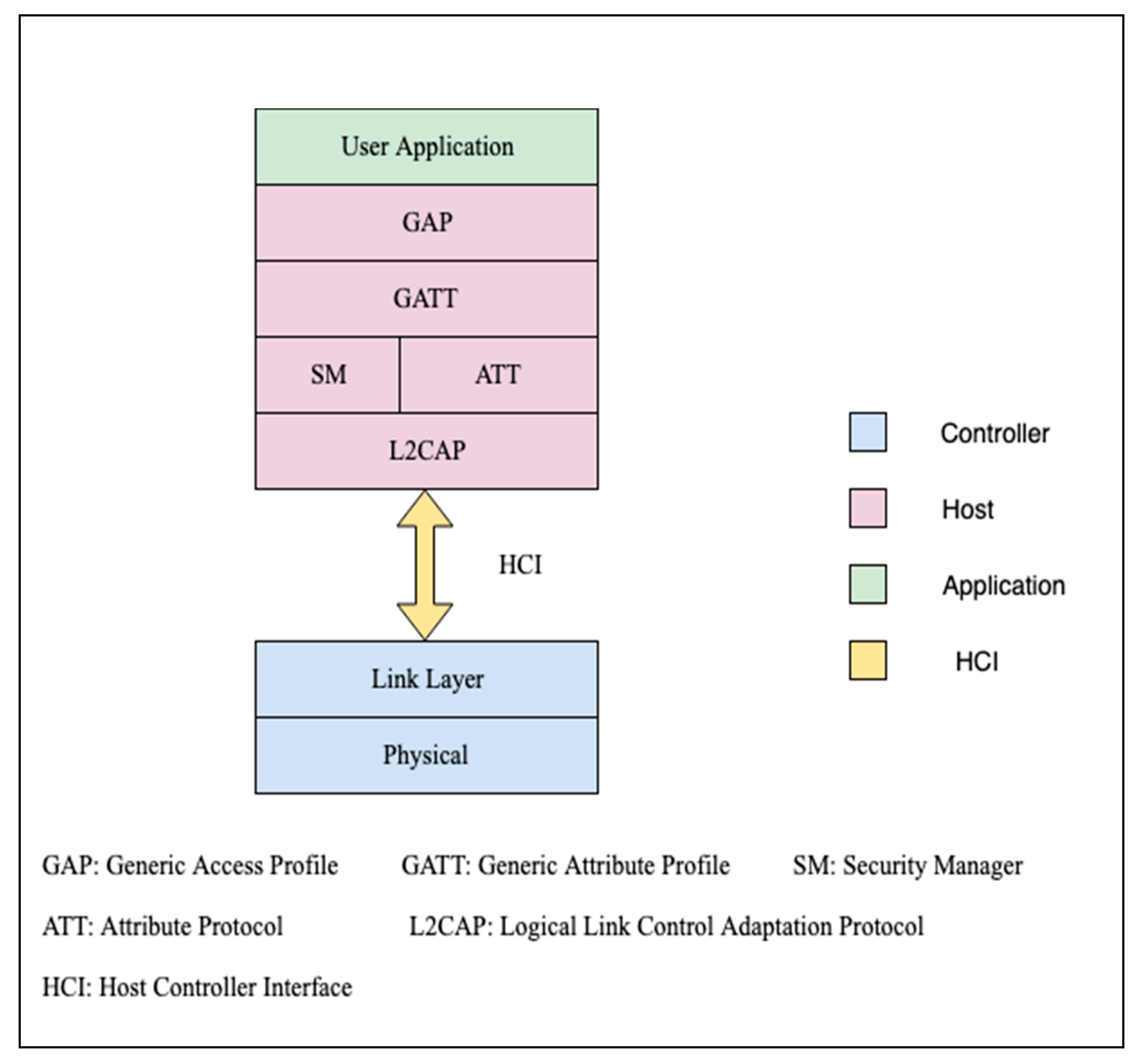
The core bluetooth framework provides the classes needed for your apps to communicate with bluetooth equipped low energy le and basic rate enhanced data rate br edr wireless technology. Guide to bluetooth security.